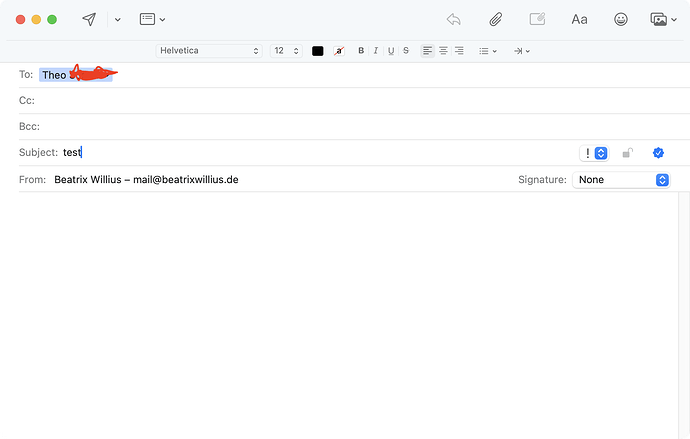
After lots of cursing I managed to create a certificate for S/MIME in Mail. But how do I encrypt an email?
According to the documentation by Apple I should be able to see a closed lock icon:
Go to the Mail app on your Mac.
Choose File > New Message.
Move the pointer over the From field, click the pop-up menu that appears, then choose the account for which you have a personal certificate in your keychain.
A signed icon (containing a checkmark) is shown in the message header and indicates your message will be signed when you send it.
Address the message to recipients.
An encrypted icon (containing a closed lock) is shown if your keychain contains a personal certificate for every recipient. If you don’t have a certificate for every recipient, click the encrypted icon in your message; an open lock replaces the closed lock, indicating the message will be sent unencrypted.
But no dice:
I made sure that the email address of the guy has a certificate.
What am I doing wrong?
Make sure that you have the public and valid certificate of the guy in your login keychain
For example:
and simply click on the gray open lock icon - it should then turn blue.
I also recommend that you have saved the recipient in your contacts, where you can also see whether you have a valid public certificate.
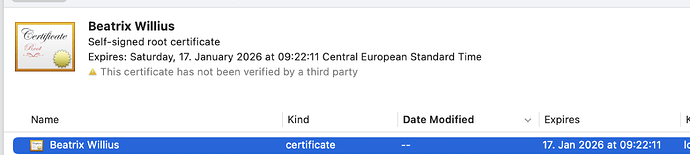
The certificate is there:
Nothing happens when I click on the blue lock icon. I only need some encrypted emails so that I can test S/MIME decryption in my app.
My certificate says “not verified”. Is this necessary? And it says nothing about MIME.
You need the public and valid certificate of the RECIPIENT as I wrote in my first post.
I wrote an email to you - with my public certificate. Hope this helps.
Oh - yes - now I see.
Yes, your certificate must be signed by a Certificate Authority.
You can create your own CA - but then you must also install your public CA certificate on every device that wants to use your S/MIME certificate. This is possible for small workgroups - and of course for testing. But is not practical for communicating with external partners.
I’ve used S/MIME in the past. It’s just not worth it. The CA’s only issue 1 year certificates, and usually don’t bother with renewals. So that means a new private key each year and having to go through all this song and dance over and over again. Plus, since you need the recipient public key, anybody sending to you needs to update their keys each year. It’s a shining example of security that is technically great, but ignores so much of the human element of security that it becomes useless.
2 Likes
I understand your points. And for my customers, it was also painful during the implementation. But now, many small and large confidential things are automatically encrypted and sent this way, and stored unreadably on the evil servers of email inbox providers. They also receive certificates with a 3-year validity period. Of course, public keys are distributed automatically - the average user rarely needs to take action. Naturally, things don’t always run smoothly. But especially in AI times, where everyone is now frantically grabbing data to analyze it - encryption is a blessing.
Just my two cents
1 Like
Fully agree. The process of getting a certificate from within the keychain is terrible (and the $%&/ thing has an internal something exception). I just need to test this for my app.